Hi!
Today we have released another little Ghidra script named ListingLover.
What is it for? Well, almost exactly one year ago, a guy named Guy ( 😀 ) published a series of wonderful IDA Pro reversing tips. One of them made me discover a feature of IDA Pro that I didn’t know existed, but that’s extremely useful:
-Reversing Tip 25/30-
Get the best from both IDA’s decompiler & disassembler by overlaying the C code on the ASM in graph view (by clicking the “/” key)#BinReversingTips pic.twitter.com/Yxrrdh9UnF— Mav Levin (@MavLevin) April 25, 2020
After pressing the ‘/’ key, IDA Pro adds the pseudo-code as comment to the disassembly listing! This is a great feature, because the decompiler facilitates reversing, but it often misses some pieces and/or makes mistakes. With this feature, it is possible to work on the disassembly listing while still benefiting from the decompiled pseudo-code.
Well, once I started using Ghidra I really missed this functionality and so I decided to build this feature in a Ghidra script.
My script adds the comments after the related disassembly instructions, using a POST comment. POST comments are perfect for this purpose, because by default they are shown in the disassembly listing and not in the decompiler pane, avoiding filling this pane with duplicate data.
An example of result is the following one:
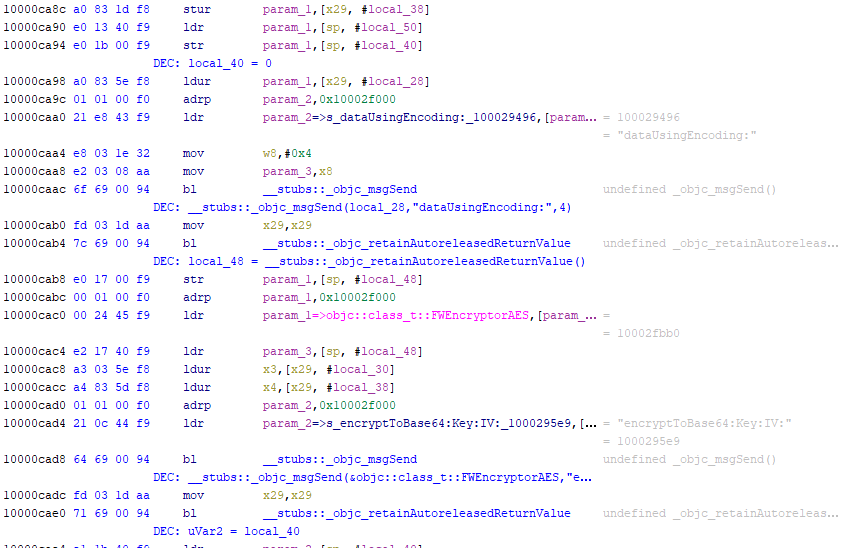
One big caveat is that this feature in IDA Pro instantly adds the pseudo-code to the disassembly listing, because probably the pseudo-code data is already associated to the disassembly listing internally. In Ghidra, instead, I had to scroll all disassembly, decompile every function and add all needed comments to the disassembly listing. These operations may require a lot of time, especially when reversing huge binaries. Based on some tests I did, ListingLover requires an amount of time comparable to that spent during initial analysis.
The best way to mitigate this issue is to launch the script in batch mode, using Ghidra headless mode (but the script can be used from the GUI as well), as follows:
$ analyzeHeadless #PROJECT_DIRECTORY #PROJECT_NAME -import #BINARY_PATH \
-scriptPath #SCRIPT_FOLDER_PATH -postScript ListingLover.java
If the analysis is executed on another machine, the results can be exported to GZF format using this script as follows:
# deleting the project folder after the export
$ analyzeHeadless #PROJECT_DIRECTORY #PROJECT_NAME -import #BINARY_PATH \
-scriptPath #SCRIPT_FOLDER_PATH -postScript ListingLover.java \
-postScript ExportToGzf.java #ARCHIVE_OUTPUT_PATH
The .gzf file can then be imported by creating a new Ghidra project and selecting the “Import file…” option.
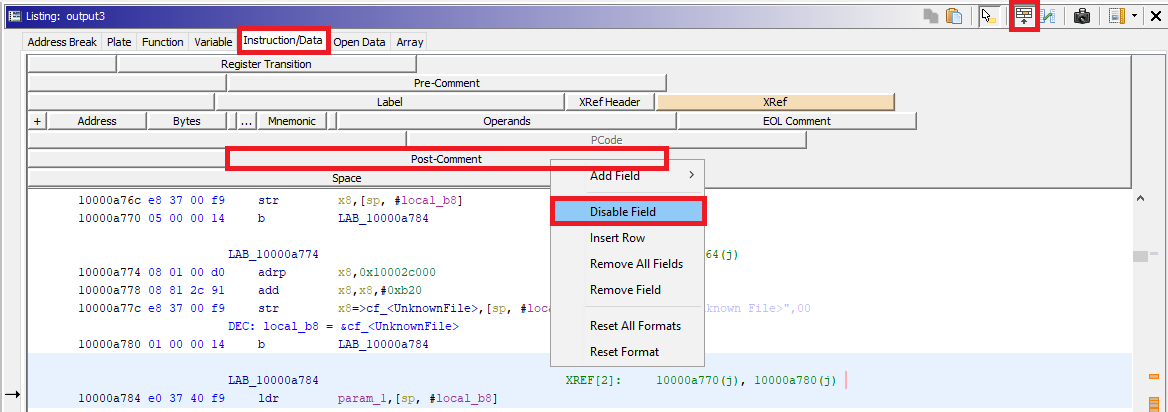
ListingLover allows to choose between “Add” and “Remove” commands, because it can also be used to remove the POST comments it inserts. Due to the huge amount of time necessary to add those comments, maybe it is better to hide Ghidra POST comments (that in my experience are rarely used) instead of removing ListingLover comments (and wasting time to insert them again when needed…). POST comments can be hidden by clicking on the “Edit the Listing fields” button of the Listing pane as follows:
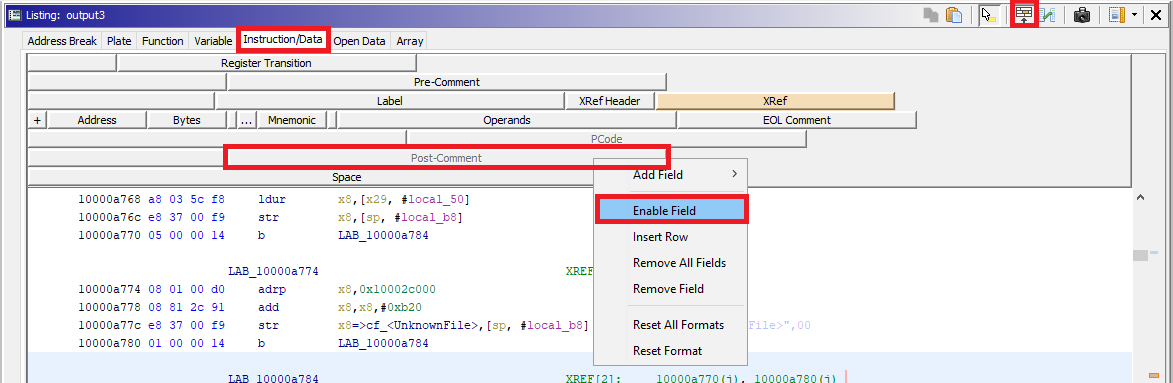
In a similar way, it is possible to enable these comments again:
The script can be downloaded from my Ghidra scripts repository: https://github.com/federicodotta/ghidra-scripts
Finally, if you are interested in reversing and vulnerability research, these Ghidra scripts we released can speed up your job considerably:
- Rhabdomancer: a simple Ghidra script to assist with vulnerability research tasks based on a candidate point strategy, against closed source software written in C/C++
- FOX: a Ghidra script to assist with reverse engineering of iOS apps. It locates all calls to objc_msgSend family functions, tries to infer the actual method that gets referenced, and updates cross-references accordingly.
- ExportToGzf: a simple Ghidra script that can be used to export a Ghidra project in gzf format, useful especially when working in headless mode
And don’t forget to check out Guy’s 30 Reverse Engineering Tips & Tricks on his blog, if you’ve never read them!
Cheers!