Hi!
I just released version 0.7 of the Java Deserialization Scanner, with a small improvement in the “Exploiting” tab.
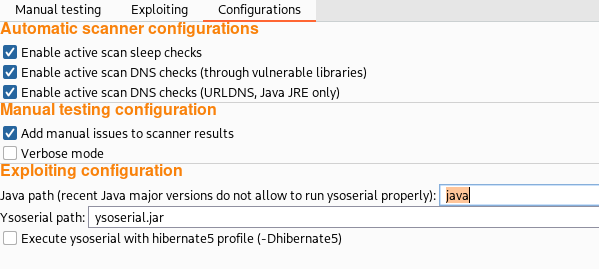
In this tab, it is possible to use the ysoserial tool to generate exploitation payloads, once the presence of a deserialization issue has been confirmed using either the “Manual testing” tab or the detection payloads added to Burp Suite’s scanner. Unfortunately, ysoserial is not entirely compatible with recent major versions of Java. To overcome this problem, it is now possible to set the full path of the Java binary used to run ysoserial in the “Configurations” pane.
The new version of the plugin can be downloaded from my repository and it will soon be added to the BAppStore.
- Source code: https://github.com/federicodotta/Java-Deserialization-Scanner
- Release: https://github.com/federicodotta/Java-Deserialization-Scanner/releases
Finally, if you are exploiting deserialization issues, you may find my ysoserial fork useful. It adds DNS, time and OS-specific EXEC attack vectors, in addition to the classic ones based on EXEC, and many output processing functions to transform, compress, and encode the output of ysoserial. Furthermore, I integrated the code of some useful ysoserial pull requests not merged in the main repository, including Isaac Sears’ XStream serializer and Nicky Bloor’s pure Java reverse shell attack vector.
Cheers!