“Rebels on the rise, we have sacrificed
Been knocked down like a poltergeist
Nocturnal by blood, in darkness we stand
We will prevail in this Rustyland”
— Krowdexx, Nocturnal Rebellion (2024)
TL;DR
I’ve released some new tools to assist with reverse engineering and vulnerability research against binary targets, based on my previous work:
- rhabdomancer: IDA Pro headless plugin that locates calls to potentially insecure API functions in a binary file. Auditors can backtrace from these candidate points to find pathways allowing access from untrusted input.
- haruspex: IDA Pro headless plugin that extracts pseudo-code generated by IDA Pro’s decompiler in a format suitable to be imported into an IDE or parsed by static analysis tools such as Semgrep or weggli.
- augur: IDA Pro headless plugin that extracts strings and related pseudo-code from a binary file. It stores pseudo-code of functions that reference strings in an organized directory tree.
They’re written in Rust and leverage Hex-Rays’s IDA Pro 9 idalib and Binarly’s idalib Rust bindings for the IDA SDK, to achieve a blazing fast, headless user experience. While working on these tools, I also contributed a number of new features to idalib.
Once upon a time in Rustyland
After approaching Rust and having explored some basic offensive applications, I decided it was time for my first serious Rust project. Last October, idalib v0.1.0 was announced, which gave me an idea: port to IDA Pro some of my Ghidra scripts that aim to streamline vulnerability research, using Rust! 🦀💡
Our REsearch team is thrilled about the new IDA v9.0! #efiXplorer is fully compatible with v9.0 and still supports IDA v8.4🚀
🔬https://t.co/WHYGifmjGSWe are thrilled to announce IDAlib — idiomatic Rust bindings for the IDA SDK 🎉 Kudos to @xorpse!
⚙️https://t.co/PLoNkf8sQn pic.twitter.com/J1no6oFatO— BINARLY🔬 (@binarly_io) October 1, 2024
Binarly’s idalib Rust bindings enable IDA Pro 9 users to develop standalone analysis tools based on the IDA SDK, using Rust in an idiomatic way and fitting Rust’s ownership model, type system, and API conventions. Tool authors can leverage the entire Rust ecosystem, so IDA Pro can be easily combined with existing Rust libraries and tools.
The availability of idalib marked the start of a new chapter in my Rust journey that saw me publish new vulnerability research tools built on top of it, and contribute a number of new features to idalib itself. And I learned a lot in the process!
My main idalib contributions to date are:
- Support for the comments API.
- Support for the (almost undocumented) bookmarks APIs.
- Support for searching text and immediate values, which incidentally led me to discover a curious bug in IDA Pro.
- Support for working with the list of strings present in a binary file.
- Various other improvements and bug reports.
We @binarly_io have just released idalib v0.2.0, an update to our @HexRaysSA IDASDK Rust bindings. It includes many new features: bookmarks, comments, and plugins APIs, hex-rays support, and documentation!https://t.co/FlBo1obu3p
Thanks to our contributors: @yeggorv, @0xdea!
— Sam Thomas (@xorpse) November 13, 2024
As a last-minute update, the idalib Rust bindings were just awarded third place in the annual Hex-Rays Plugin Contest! 🎊 This is a well-deserved recognition, and I’m happy to be a humble contributor of this awesome project 💚
We are thrilled to announce the winners of the 2024 Hex-Rays Plugin Contest!
🥇1st Place: hrtng
🥈2nd Place: aiDAPal
🥉3rd Place: idalib Rust bindingsCheck out our reviews of the winners and other notable submissions here: https://t.co/XgkQHfktAF
Huge thank you to all… pic.twitter.com/rw1qzmLjdf— Hex-Rays SA (@HexRaysSA) February 17, 2025
The maintainers of idalib are wonderful people, and I encourage you to contribute to its development. Sam has also published some related repositories that you should check out as well:
- parascope: a weggli ruleset scanner for source code and binaries.
- weggli-ruleset: a utility crate to help manage weggli patterns, such as those I published last year.
- wegglix: a weggli fork updated and modified for a more pleasant library experience.
Now, before we take a look at the new tools, as customary in this series, let’s pick an appropriate soundtrack and recommend some learning resources to deepen our knowledge of Rust.
Hack with a soundtrack
Today’s soundtrack to make you hack harder is Krowdexx‘s set at the Rustyland Festival 2024. How appropriate! 🙅♂️🙅♂️
Learning resources
As usual, the main takeaway should be to get your hands dirty as soon as possible and hack together some code that makes you happy and, who knows, perhaps even proud. And have fun doing it! This is super important, at least for me…
With that in mind, the best Rust learning resources I perused during these past few months are:
- The Rustonomicon. Prepare for a wild ride beyond the boundaries of our reality. It’s time to read the ‘nomicon, especially if you’re going to dabble in the dark arts of unsafe Rust like I keep doing for some reason…
- Crust of Rust. I’m a No Starch Press fan and as such I can’t help but recommend Rust for Rustaceans, although this seems to be one of those rare cases where I actually prefer the movie version 🤷
- Code Like a Pro in Rust. This book and its beginner-oriented companion Rust in Action are a must read for all serious Rust programmers.
- How To Code It. This website and newsletter feature a growing collection of high-quality practical guides that will show you how to take your Rust to the next level.
- Pretzelhammer’s Rust Blog. This GitHub repository features well-curated educational content for Rust beginners and advanced beginners, such as a tour of standard library traits and a popular article on lifetime misconceptions.
- Corrode Blog. This blog features an ongoing series of articles about idiomatic Rust and best practices, including some detailed tips for faster builds and long-term project maintenance.
- Type-based Rust cheatsheet. Compact cheatsheet organized by Rust type, packed with useful ways to process and convert them. Not particularly advanced, but still a handy companion to cheats.rs.
- Rust Cookbook. A collection of simple examples that demonstrate good practices to accomplish common programming tasks, using the crates of the Rust ecosystem.
- Publishing on crates.io. This and some other useful resources will come in handy when it’s time to publish your first crate on crates.io 🎉
- This week in Rust. This is the main source to stay up to date with events, learning resources, and recent developments in the Rust community.
As a final note, on the occasion of its 10th edition I enrolled to the Advent of Code 2024, with some amazingly ugly code! 😅 It was challenging and fun, and I can now tell without a shadow of a doubt that these puzzles aren’t really my cup of tea…
It’s now time to introduce my brand new tools built on top of idalib 🥁
Meet rhabdomancer
Rhabdomancer
/răb′dəmăn″-sər/
Someone who uses a divining rod to find underground water.
Rhabdomancer is the Rust port of one of my original Ghidra scripts, that I’ve described in my article “Automating binary vulnerability discovery with Ghidra and Semgrep”.
It’s an IDA Pro headless plugin that locates calls to potentially insecure API functions in a binary file. Auditors can backtrace from these candidate points to find pathways allowing access from untrusted input. Its main features are:
- Blazing fast, headless user experience courtesy of IDA Pro 9 and Binarly’s idalib Rust bindings.
- Support for C/C++ binary targets compiled for any architecture implemented by IDA Pro.
- Bad API function call locations are printed to stdout and marked in the IDB.
- Known bad API functions are grouped in tiers of badness to help prioritize the audit work.
- [BAD 0] High priority – Functions that are generally considered insecure
- [BAD 1] Medium priority – Interesting functions that should be checked for insecure use cases.
- [BAD 2] Low priority – Code paths involving these functions should be carefully checked.
- The list of known bad API functions can be easily customized by editing conf/rhabdomancer.toml.
Additional information on rhabdomancer’s features and usage is available at crates.io and in the official documentation.
Let’s install it and take it for a spin! The easiest way to get the latest release is via crates.io:
- Download, install, and configure IDA Pro (see https://hex-rays.com/ida-pro).
- Download and extract the IDA SDK (see https://docs.hex-rays.com/developer-guide).
- Install rhabdomancer as follows:
$ export IDASDKDIR=/path/to/idasdk90 $ export IDADIR=/path/to/ida # if not set, the build script will check common locations $ cargo install rhabdomancer
Only the UNIX target family is currently supported. I might port the tool to Windows if there’s some interest.
Now let’s run rhabdomancer against a binary file. Our target of choice is the legendary dtprintinfo SPARC binary, that was featured in countless advisories, exploits, talks, and articles (even in Phrack!) by yours truly and other old-school hackers over the years… Here’s to CDE! So long, and thanks for all the shells! 🥂 #️⃣
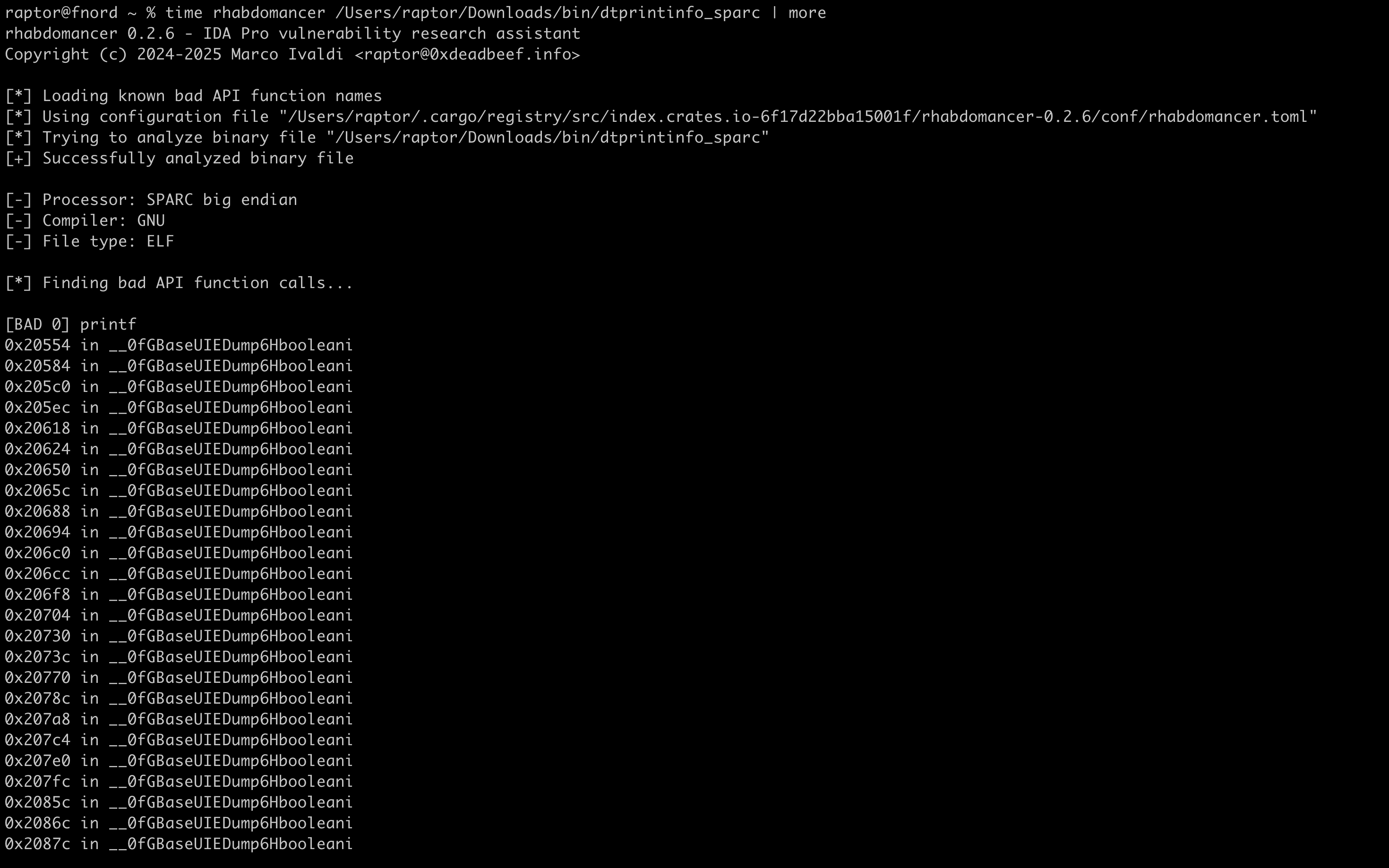
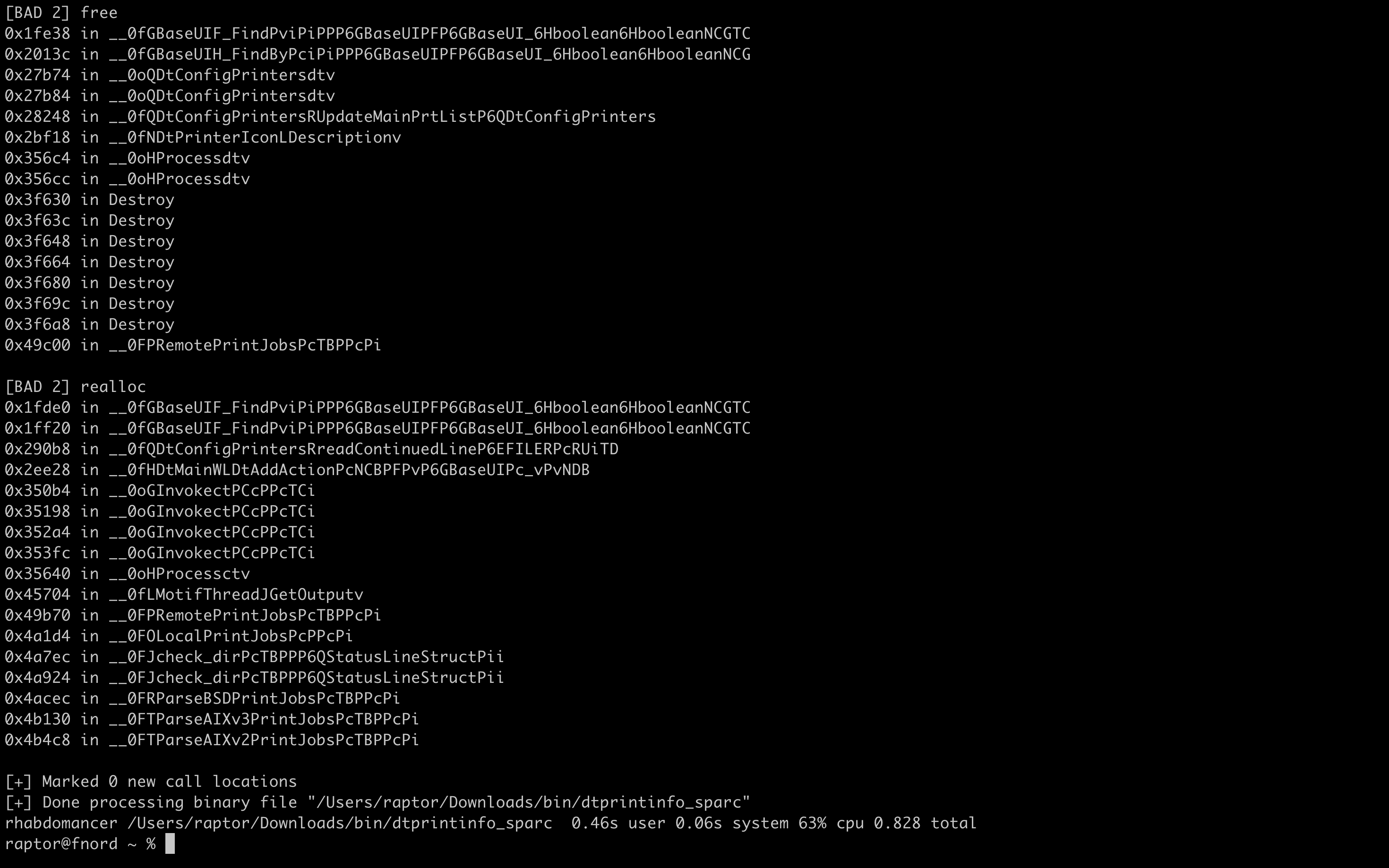
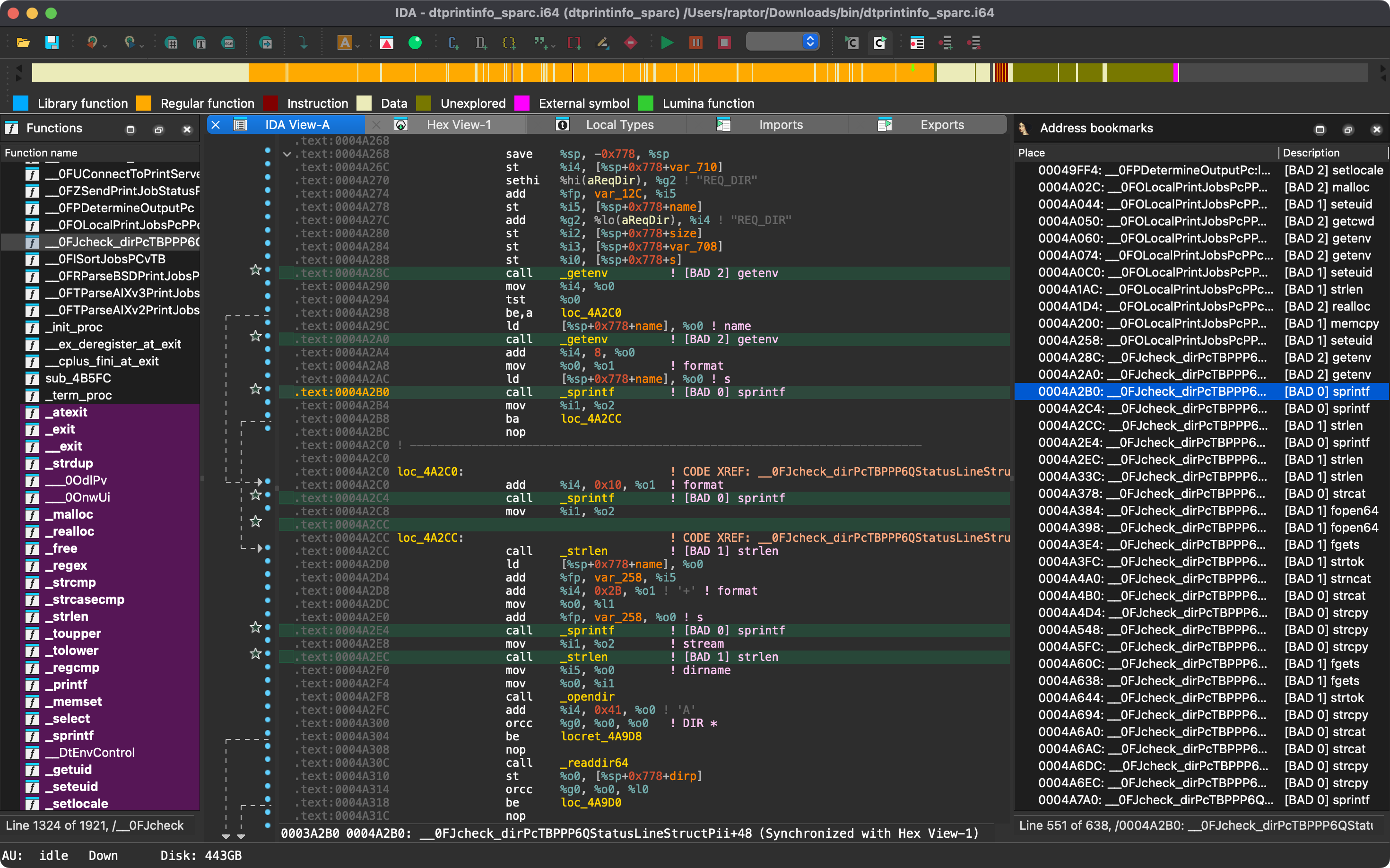
That’s it! We don’t have enough space for a full code walkthrough. However, you can browse the source code on GitHub:
It should be easy to follow. You can even check all commits to inspect my reasoning behind each implementation choice, if you’re so inclined.
What about haruspex and augur?
Haruspex
/hə-rŭs′pĕks″, hăr′ə-spĕks″/
A priest in ancient Rome who practiced divination by the inspection of the entrails of animals.
Augur
/ô′gər/
One held to foretell events by omens.
Haruspex is the Rust port of another Ghidra script of mine. It’s an IDA Pro headless plugin that extracts pseudo-code generated by IDA Pro’s decompiler in a format that should be suitable to be imported into an IDE or parsed by static analysis tools such as Semgrep or weggli. Its main features are:
- Blazing fast, headless user experience courtesy of IDA Pro 9 and Binarly’s idalib Rust bindings.
- Support for binary targets for any architecture implemented by IDA Pro’s Hex-Rays decompiler.
- Pseudo-code of each function is stored in a separated file in the output directory for easy inspection.
- External crates can invoke decompile_to_file to decompile a function and save its pseudo-code to disk.
Additional information on haruspex’s features and usage is available at crates.io and in the official documentation.
Installation and usage are akin to what I’ve described earlier for rhabdomancer. The most notable difference is that haruspex can also be used as a library by third-party crates to decompile specific functions and save pseudo-code to disk. An example of this is augur, another IDA Pro headless plugin that extracts strings and related pseudo-code from a binary file. I encourage you to check it out.
Coming back to haruspex, let’s try it out against a sample binary. This time, our target of choice is an ARM aarch64 binary distributed with recent Zyxel appliances, part of an ongoing vulnerability research effort (stay tuned to our blog to not miss any updates on this topic).
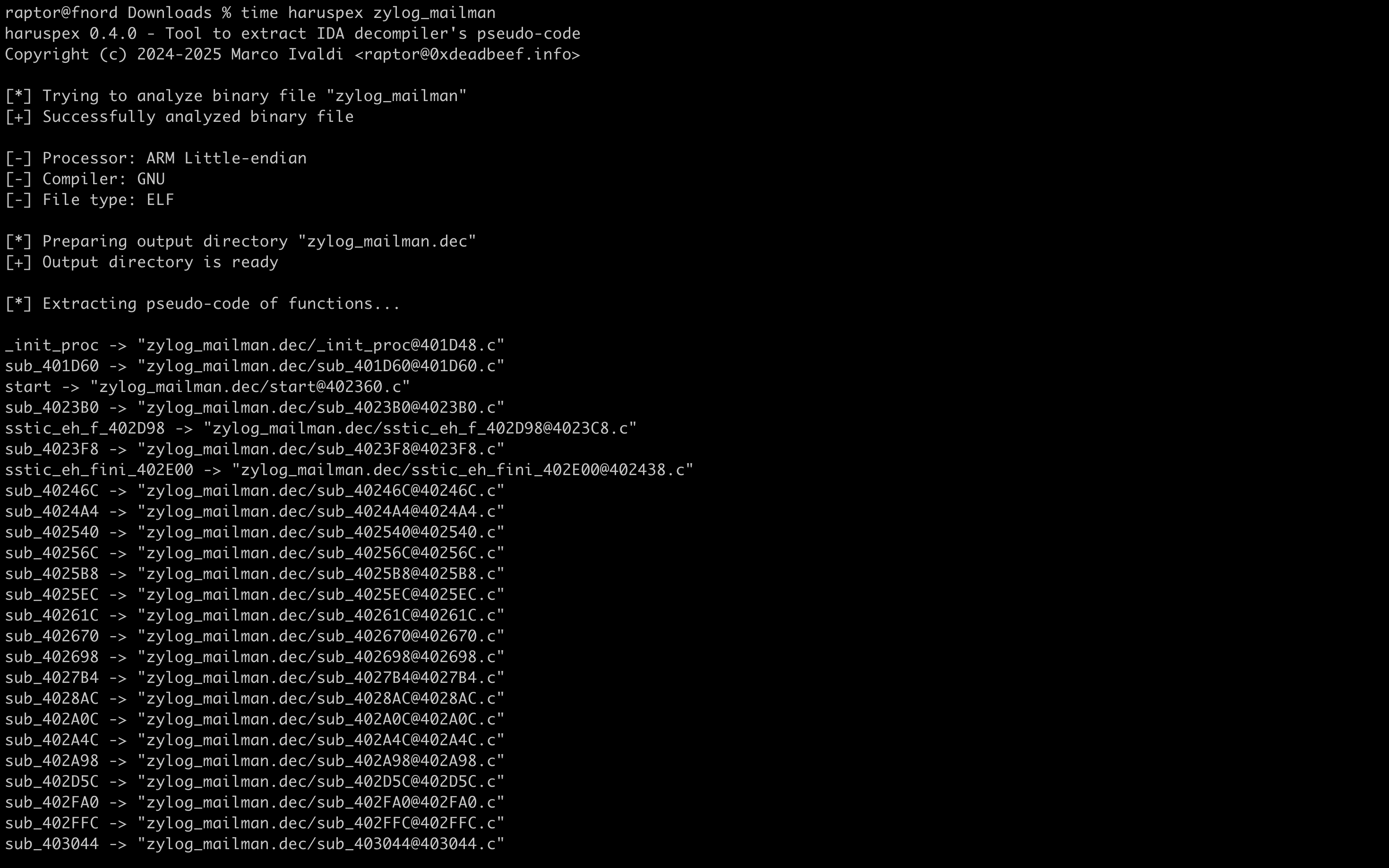
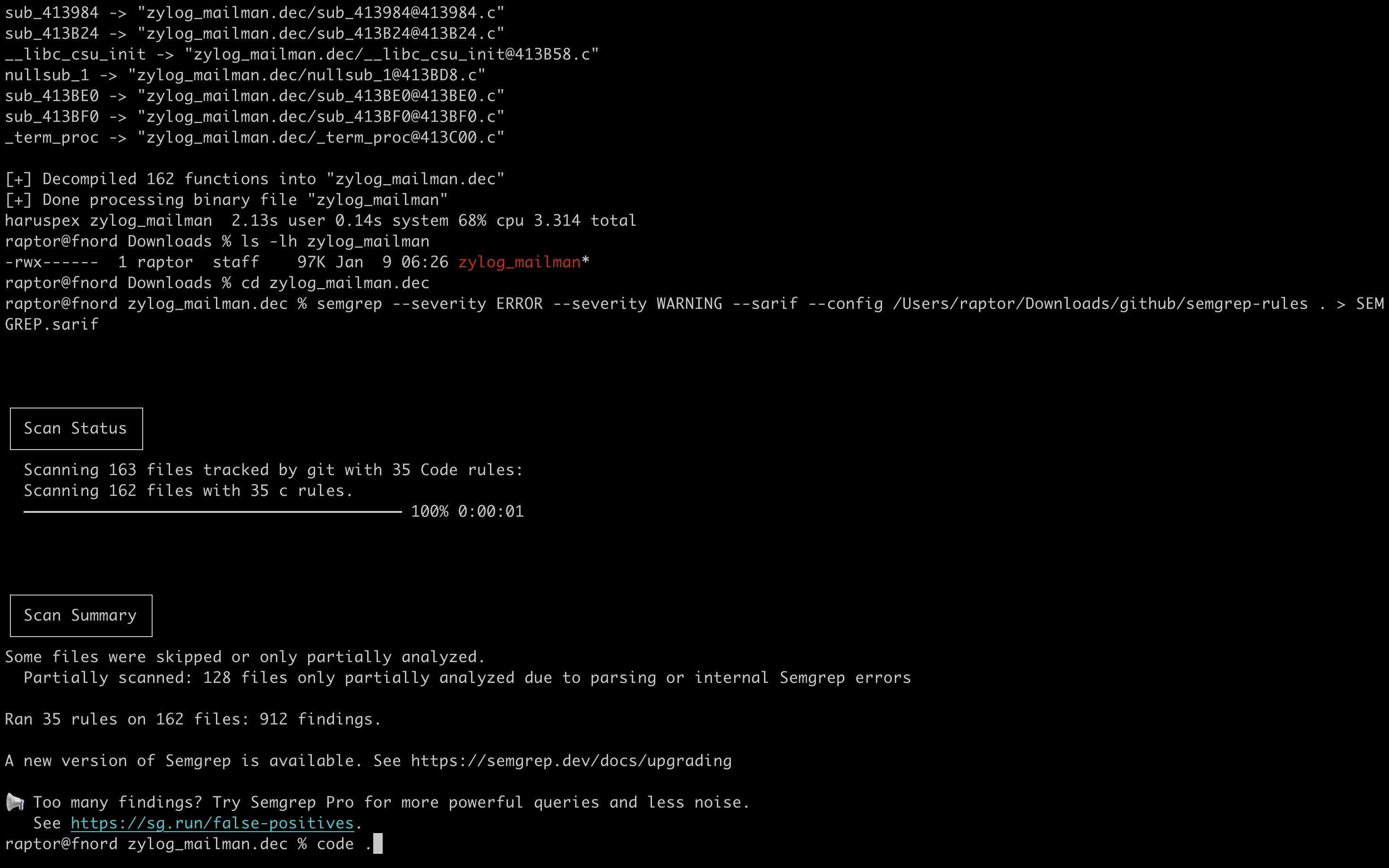
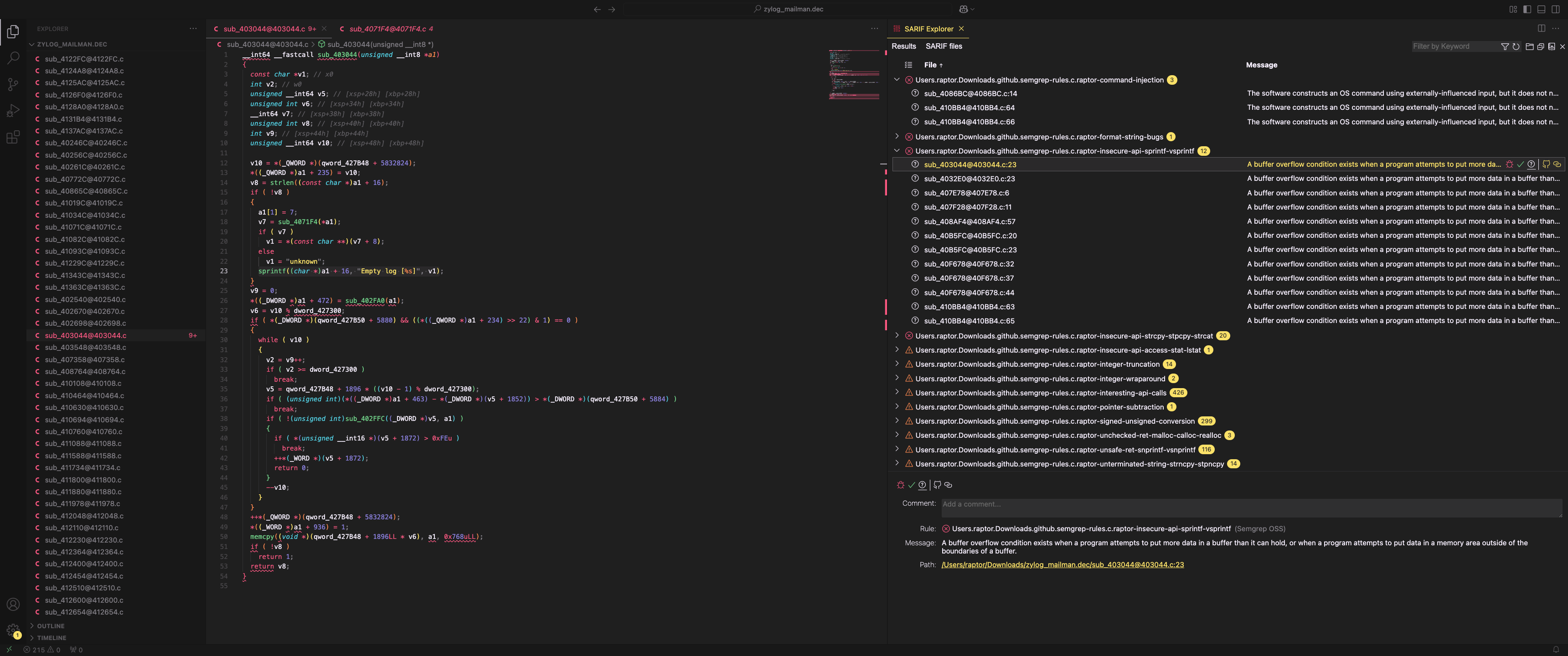
For additional information on my vulnerability research tools and methodology, please refer to the following articles:
- https://security.humanativaspa.it/semgrep-ruleset-for-c-c-vulnerability-research/
- https://security.humanativaspa.it/automating-binary-vulnerability-discovery-with-ghidra-and-semgrep/
- https://security.humanativaspa.it/big-update-to-my-semgrep-c-cpp-ruleset/
- https://security.humanativaspa.it/a-collection-of-weggli-patterns-for-c-cpp-vulnerability-research/
You can browse haruspex’s and augur’s source code on GitHub:
Conclusion
The award-winning idalib Rust bindings open endless possibilities. Developers can leverage the entire Rust ecosystem to combine IDA Pro with existing Rust libraries and tools, such as weggli, or use it as part of larger static/dynamic analysis pipelines alongside, for example, libafl.
I would like to thank idalib’s maintainers at Binarly and especially Sam L. Thomas (@xorpse), who made me feel welcome since my first pull request. You’re awesome ✊
I hope this article has served as a useful introduction to idalib, and that you’ll consider building your own tools on top of this powerful Rust library. Meanwhile, you can download my brand new vulnerability research tools from lib.rs, crates.io, or GitHub.
I’ll keep working on my tools and on idalib itself to add new features and improve the current ones. Our Rust journey continues… Until next time!