“If you shame attack research, you misjudge its contribution.
Offense and defense aren’t peers. Defense is offense’s child.”
— John Lambert
TL;DR
Last month, some of the world’s top security researchers came together on the Microsoft campus for the first-ever Zero Day Quest Onsite Hacking Event, an invite-only gathering focused on fostering collaboration, exchanging ideas, and finding vulnerabilities across Microsoft’s AI and Cloud programs.
From nonstop bug hunting sessions and deep dives with Microsoft engineers to exclusive social events like dinner at the Space Needle and a Seattle Mariners game, Zero Day Quest was equal parts security research and community building.
As one of last year’s highest ranking Azure security researchers and Most Valuable Researcher (MVR), I was selected to participate in this event based on my expertise and contributions to Microsoft. Here’s the story of how I qualified and my experience at the Zero Day Quest.
As a bonus, after ZDQ I’ve also been a guest at the BlueHat Podcast, Microsoft’s podcast that hosts conversations with researchers and industry leaders working to secure the planet’s technology and create a safer world for all. Catch my episode here! 🧢
From Unix to Azure
It’s been one month since I attended the inaugural Zero Day Quest, the largest live hacking event of its kind that brought together top security researchers from around the world to find the highest-impact vulnerability scenarios in Microsoft’s AI and Cloud.
But how did a seasoned Unix hacker like me qualify for a Microsoft event in the first place? Long story short, some time ago I became interested in source code review. I built some tooling to automate part of it, and in 2023 I audited the most popular open-source IoT operating systems: Zephyr, RT-Thread, RIOT, FreeRTOS, and more…
At some point, I stumbled upon Azure RTOS. In December 2023, I reported to MSRC a few vulnerabilities in this OS, two of which were found in a couple of hours of code review and were fixed right away. They alone earned me a whopping 240 points that landed me in the top positions of their quarterly leaderboards!
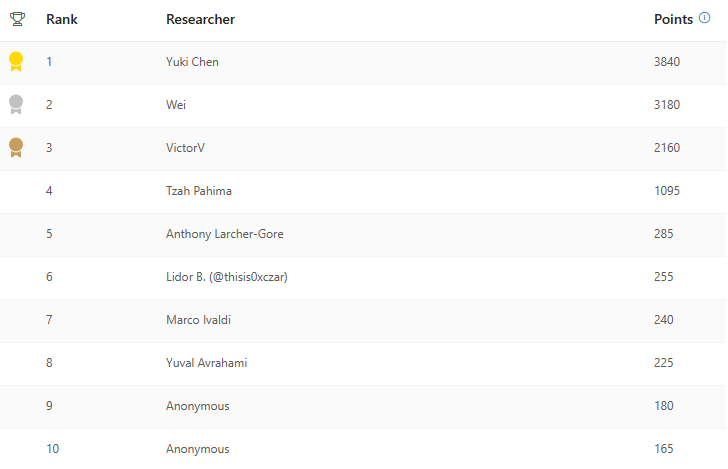
Shortly after my first bug submissions, Azure RTOS was handed over to the Eclipse Foundation and became Eclipse ThreadX. Therefore, all other vulnerabilities I reported in this software were not handled by MSRC anymore. In addition, I wasn’t awarded a bounty because Azure RTOS had been declared out of scope for the Azure bug bounty in August 2023. It’s not like I was expecting a bounty anyway, I’m more old school than that. I’m already happy if I don’t get sued 🤷
But I digress. The ease with which I was able to climb the MSRC leaderboard rankings became an incentive to look deeper into the Microsoft Researcher Recognition Program. This brought me to audit the source code of other projects under the Azure organization on GitHub.
Who wants to be an MVR?
Between January and April 2024, I reported more than 50 vulnerabilities in 20 Azure products. My research paid off with a substantial bounty and sparked a number of security improvements in the Azure ecosystem.
My vulnerability reporting spree of early 2024 resulted in me being featured at the top of MSRC quarterly leaderboards again.
Congrats! Cheers to your ongoing success and contributions to enhancing security. 🥂
— Security Response (@msftsecresponse) April 17, 2024
But all good things must come to an end… After a few disagreements and some frustrating exchanges with MSRC, at the end of April 2024 I gave up and stopped reporting vulnerabilities to Microsoft. Still, in August 2024 my spare-time hobby was rewarded with the 25th place in the annual MVR leaderboard! Not too bad for a middle-aged Unix hacker 😜
Here are a few stats of the time I dedicated to vulnerability research in that 4-month period:
- 24 hours spent auditing Azure RTOS / Eclipse ThreadX (not including the time dedicated to vulnerability disclosure)
- 70 hours spent auditing other Azure software (not including the time dedicated to vulnerability disclosure)
- 14 hours spent auditing other open-source Microsoft software before giving up
I recently discovered that another well-known security researcher, VictorV, had a similar experience with the Microsoft Azure bounty program. Probably at least in part due to the sheer volume of our vulnerability reports combined together, open-source software was eventually declared out of scope. It was good while it lasted…
Welcome, hackers
Fast forward to early 2025, when I received an email from Microsoft with an exclusive invitation to their first-ever Zero Day Quest event!
Well… It looks like I’m going to Redmond! ✈️ 🇺🇸
Many thanks to @msftsecresponse for the exclusive invitation to their Zero Day Quest Onsite Event. Looking forward to meeting fellow top-notch security researchers from around the world and having fun!https://t.co/bTjhp8XhJB pic.twitter.com/tHKDCNfi2w
— raptor@infosec.exchange (@0xdea) February 7, 2025
How could I’ve missed this extraordinary opportunity to peek behind the scenes of MSRC and meet fellow top-class security researchers from around the world?
I registered for the event, booked my flights, and April came quickly. I found myself transported into this weird but surprisingly successful mix of corporate culture and hardcore hacking.

There were attendees of all ages, from every corner of the world. I believe I was the oldest one among the researchers, a full 30 years older than the youngest participant 😱

I had so many extraordinary encounters that I can’t possibly mention them all: from the 17 years old prodigy (see above) who raked in what ought to be the highest payout ever awarded in an event like this to the music producer from Argentina with a touching life story who sported a Microsoft tattoo. From one of the most prolific bug hunters in the history of the Microsoft Researcher Recognition Program to the wine connoisseur of Ukrainian descent. From the full-time bug hunter who travels the world to the paranoid hacker who avoided cameras and had an obviously fake name (I’m joking, mate 😂). And many more…
Not to mention Microsoft’s staff that took good care of us. I believe I made some real friends there!

I even got to briefly meet the great Mark Russinovich of Sysinternals fame 🤩

Old dog, new tricks
So, for me, the best part of ZDQ was definitely the people I met. A close second was the constant pampering and the high-quality swag. I seriously risked not being able to close my suitcase when heading back to Italy!

Beside branded clothes and expensive gadgets, we got a full range of benefits, such as a professional photo shooting, a massage parlor, a bar stacked with good coffee and drinks for all tastes, a steady supply of food, and of course the amazing evening events: a thoroughly American baseball match, dinner at one of the best Italian restaurants in the area, a last-minute city tour of Seattle, and the closing ceremony at the iconic Space Needle!
There was really a lot to unpack, both physically and metaphorically 😅

What else is there to say? Even though the scope that was picked for the event didn’t particularly agree with my specific talents, I can tell that this old dog has learned a couple of new tricks! It feels good to be #StillHacking after almost three decades 🐶
The BlueHat Podcast
After the event, I joined Nic Fillingham and Wendy Zenone in a new episode of Microsoft’s BlueHat Podcast. You can catch it here!
I shared raptor’s origin story, from my first computer and hacking as a teenager to becoming part of the worldwide security research community. We chatted about my first-ever CVE, overlooked vulnerabilities that continue to pose significant risks today, Active Directory and password security, my unexpected journey into bug bounty hunting and my involvement in the Zero Day Quest, how to learn new things, mentorship and positive leadership, and of course pineapple pizza 🍍🍕

It’s been truly special, thank you for having me! 🫶